As of 2022, WordPress is the most popular CMS, powering over 450 million websites. One of the reasons behind its popularity is the fact that it’s open-source. Unfortunately, that popularity comes at a cost. Because anyone can build a plugin or theme, WordPress isn't free from vulnerabilities. Based on WP Scan’s data, as of writing there are close to 30,000 WordPress security vulnerabilities.
Of course, while that number may seem mind-boggling, you don’t have to worry about all 30,000 to keep your site secure. The vast majority of these are outdated and already patched. Others were relevant to a tiny fraction of people who were using a specific plugin or theme.
In reality, most WordPress security vulnerabilities fall into just a few distinct categories. The good news is, as long as you follow key security good practices, you’ll be safe from most of them.
Table of Contents
1. WordPress Plugins and Themes
2. WordPress Login Page
3. Denial of Service
4. SQL Database Injections
5. Malicious Software (Malware)
6. Cross-Site Scripting
7. Hotlinking to Your Content
8. The Human Factor
9. Start Fixing WordPress Security Vulnerabilities Today
1. WordPress Plugins and Themes
Probably the broadest category is all the vulnerabilities in WordPress themes and plugins. Out of 1628 new vulnerabilities disclosed in 2021, 97.1% were related to WordPress plugins. The second spot, with 2.4% of wordpress security vulnerabilities belonged to themes.
Typically, there are three reasons why a theme or plugin is vulnerable:
- It’s been poorly designed right from the scratch.
- It didn’t receive security updates for some time and became vulnerable.
- Its code has been modified by a third party. This is common for plugins and themes downloaded from unofficial sources.
How to Fix This Vulnerability:
There’s one key thing to do here: ensure all your plugins and themes come from an official source - and keep them updated. Naturally, you have to trust that developers will keep delivering updates. So if you notice that you stopped getting security updates (like in the example below), it’s time to make a switch.
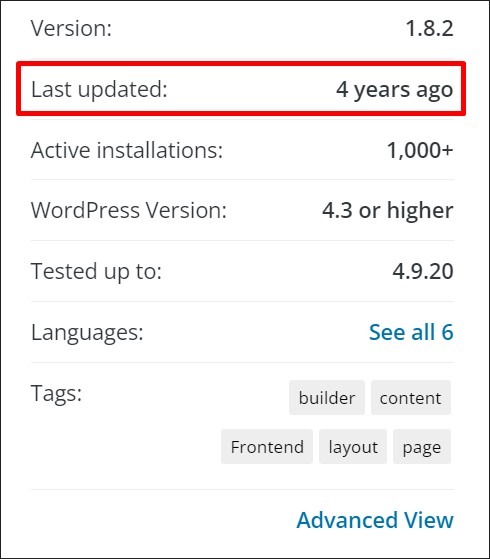
Of course, keeping all your plugins and themes updated manually can be troublesome. Especially if you own more than one WordPress website.
This is where a plugin like WP Blazer with its Plugin and Theme Management feature can help you out. With WP Blazer, you can manage (and update) all your plugins and themes using one central dashboard. No matter how many websites you’re running.
2. WordPress Login Page
The next on the list of WordPress security vulnerabilities is its login page. Out of the box, the WordPress login page can be found at /wp-admin and /wp-login.php slugs. Note that leaving it at its default location gives others instant access to your login form.
Of course, they still need a password - which is the next key WordPress login vulnerability. An easily accessible login page and a password that’s easy to break are a recipe for disaster. Especially since most hackers don’t try to guess a password manually. Rather, they use bots that can try hundreds of combinations of the most common passwords.
How to Secure Your Login Page:
There are several things you can do to secure your login forms:
- Change the wordpress login page address. You can do that with a bit of coding or using a plugin like WPS Hide Login.

- Add captcha and/or limit login attempts. Banning users after a few tries can prevent hackers from using bots that try to guess your password.
- Enforce strong and unique passwords from your team and use one yourself. You can also use tools like LastPass. It helps manage unique and strong passwords for different websites and services.
- Force users to verify their login using a separate tool (two-factor authentication). The easiest way to do that is using a plugin such as Two Factor Authentication. It supports the most popular 2FAs from both Apple and Google.
- Change user IDs to something unique. Never use your email address or generic words such as “admin” as a login ID.
3. Denial of Service
Denial of service attacks don’t harm your website files or data and its another one type of wordpress security vulnerabilities. Rather, their aim is to flood your website with so much traffic that it crashes the server. The goal? Make your website inaccessible.
Usually, it’s not a problem to restore the server and block the attack after it happens. But every minute that your site is down costs you money in ad or sales revenue. And the losses are more than short-term. Why?
Most people who see that your site is down will likely never come back. This means you’re losing both current and future recurring visitors.
One of the reasons why DoS attacks are so hard to prevent is that often, they’re performed using many servers. This is what’s known as distributed denial of service (DDoS) attacks. It’s also one of WordPress security vulnerabilities that has nothing to do with themes or plugins.
How to Reduce the Risk of DDoS:
- Avoid poor-quality shared hosting. Instead, find a hosting provider who’s using hardware capable of mitigating the risk of DDoS. Popular features include server-side intelligent switches and routers. Also, ensure that your hosting provider is responsive and easy to reach out to in case of an attack.
- Add an extra layer of protection such as Cloudflare.
- Use a WordPress security plugin with extra DDoS protection such as Wordfence.

- Create an SOP outlining what to do in case of an attack. This will help you stay calm and get your site up and running faster.
- Block pingbacks and trackbacks by blocking XML-RPC functionality. You can do that by adding the following to your .htaccess file:
# START XML RPC BLOCKING
Order Deny,Allow
Deny from all
# FINISH XML RPC BLOCKING
Keep in mind that the latter is more about preventing your site from getting used in a DDoS chain. As such, it won't protect it from getting DDoSed.
4. SQL Database Injections
Not just your plugins and themes are a potential backdoor into your website. Another key vulnerability is your SQL database where hackers try to inject it with SQL code. The goal is to exfiltrate data or get instant access to privileged user accounts.
The biggest danger of SQL injections lies in the fact that they’re easy to execute on insecure websites. Moreover, when successful, they often give attackers full access, bypassing all authentication measures.
Thankfully, database injections are one of the easiest WordPress security vulnerabilities to fix. That's if you know what you’re doing, of course:
How to Prevent Database Injections:
- Collect only necessary user input. The fewer input forms you have on your website, the easier it is to keep everything secure.
- Ask users to “select” rather than input. If possible, switch classic input forms to those where users can select an answer. This works great for data such as dates or locations.
- Ensure all your forms validate input data. This prevents users from typing anything they want into the input fields.
- Scan your site with a tool like WordPress security scanner to check it for SQL injections.
- Block spam comments using plugins like Antispam Bee. Don’t forget that a comment form is still a form and as such can be vulnerable. Another thing you can do to reduce spam is to switch to an alternative commenting system such as Disqus.

5. Malicious Software (Malware)
Malware is one of the most widespread security risks on the Internet. As such, only a small percentage of it is targeting WordPress websites.
Usually, its “goal” is to gain access to sensitive data (such as credit card data) or the website itself. Other times the attacker uses it to force redirects or downloads on people who visit your site.
Often, malware gets “planted” in nulled plugins or themes. They can also come with other files that you upload to your website, or get planted by one of your site’s users.
How to Secure Your Site from Malware:
- If you have many people working on your website, limit uploading privileges.
- Never use plugins and themes from unauthorized sources.
- Perform periodic malware scans using tools such as Anti-Malware Security and Brute-Force Firewall.

6. Cross-Site Scripting
XSS attacks are one of WordPress security vulnerabilities similar to SQL injections. But, rather than trying to access the database, the attacker injects the code into the backend. The goal is to alter your website’s functionality.
Of course, that doesn’t mean they’re not as dangerous as SQL injections. For example, the attacker can use XSS to add harmful links or force redirects. They can also fake contact or shopping forms to steal users’ personal or payment data.
What to Do to Prevent XSS Attacks:
- Keep your plugins, themes, and all WordPress core files up-to-date.
- Never add WordPress themes and plugins from unknown sources.
- Deploy a web application firewall (WAF). The easiest way to do that is via a plugin such as Sucuri.
7. Hotlinking to Your Content
Not all WordPress security vulnerabilities result in your website getting "hacked". Unlike the other ones, hotlinking relates to the way others share your work. Imagine you’re a small site and a website with thousands of visitors links to your content. Sounds like a dream come true? Well, that depends on how they link to what you share.
If they download your work, upload it to their server, and then post it (and give you credit for it), then that’s fine. Of course, as long as your content isn’t restricted from getting shared in any way.
But if it’s not - you get a mention and a backlink, and your site benefits.
The problem arises when they decide to embed it instead. In this case, you’ll be the one charged for all the bandwidth. And if your hosting package is small, this could crash your servers. Especially if someone embeds multiple images from your site.
The upside is that hotlinking is rarely used to crash your servers and website. Most of the time, it’s used by inexperienced webmasters who don’t understand the consequences.
How to Secure Your Content Against Hotlinking
- Use a WordPress CDN (Content Delivery Network) such as KeyCDN.
- Enable server-side hotlinking protection. This will depend on whether your website is running on Apache or Nginx.
If it’s Apache, add the following to your .htaccess file:
/* WordPress Hotlinking Block: */
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?yourwebsite.com [NC]
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?google.com [NC]
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?facebook.com [NC]
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?twitter.com [NC]
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?other-websites-go-here.com [NC]
RewriteRule \.(jpg|jpeg|png|gif)$ - [F]
IAnd if it’s Nginx, simply edit the config file and add the following:
location ~ .(gif|png|jpeg|jpg|svg)$ {
valid_referers none blocked ~.google. ~.bing. ~.yahoo. yourdomain.com *.yourdomain.com;
if ($invalid_referer) {
return 403;
}
}
- Use a WordPress plugin. As of writing, there are no up-to-date standalone plugins that protect from hotlinking. And don't forget that old plugins a major WordPress security vulnerability. Thankfully, there are a few security plugins offering hotlinking protection. These include All In One WP Security & Firewall and BulletProof Security.

- Speaking of plugins, they can be used to watermark your images - which is one of the ways of protecting your content. But while watermarks can prevent a theft, they won’t stop those embedding the content in good faith.
- Once you identify hot-linked content, your best bet is to rename the file. Also, if someone embedded your content in good faith, reach out to them. Thank them for their interest in your content and explain how they should share it so that it’s a win-win.
8. The Human Factor
Lastly, we get to one of the most dangerous WordPress security vulnerabilities of all - your team members. Yet, the human factor is often overlooked or its importance is minimized.
Often, it’s not the admin but someone from the team whose account gets compromised. People can make mistakes. They can become victims of social engineering. Or they can do the damage on purpose (for example, in revenge).
We’ve already discussed a couple of ways in which your team members can increase your site's security. These include strong passwords, password managers, and keeping website themes and plugins up-to-date.
But, there’s more you can do to protect your site:
- Clearly define user roles - and don’t give people more permissions than they need. Giving everyone admin rights is a recipe for disaster. The more access people have, the more damage can occur in case their account gets compromised.
- Keep a list of security good practices and ensure all your team members know and apply them. And, of course, don’t forget to lead by example!
- Create security protocols and SOPs for people to follow - and ensure they’re actually doing this. The SOPs and protocols don’t just help your team members follow the good practices. They also help protect your team against social engineering. When your team members have a clear set of rules and steps to follow, they’re unlikely to ignore them. Just keep in mind it’s not a bullet-proof solution.
Start Fixing WordPress Security Vulnerabilities Today
Some people say WordPress isn’t safe. The real problem is not the platform but the way people are using it. If you follow the right good practices and use common sense, it's easy to keep your site secure. And, of course, you want to make sure your site is always up-to-date.
With WP Blazer’s WordPress Plugin/Theme Management, you can do that in one convenient dashboard. And it doesn't matter if you own one site or five or twenty. Not to mention built-in backups, malware scanners, and SSL management. Check out WP Blazer’s 14-day trial and start securing your site today. Fix most common WordPress vulnerabilities in a few clicks and protect your hard work!
