If you’ve been administering a site for any time, you’ve likely heard of a variety of ways hackers can use to gain access to it. For our community, one prevalent method is a WordPress SQL injection attack.
They say knowledge is power, so I’m going to take some time and educate you about everything you need to know about a WordPress SQL injection, including what it is, how to avoid it, and what to do if it happens to you.
Let’s get started.
Table of Contents
1. What is SQL?
2. Why It’s Important to Guard Against WordPress SQL Injection Attacks
3. What is a WordPress SQL Injection Attack?
4. How Does a WordPress SQL Injection Attack Work?
5. How to Prevent an SQL Injection
6. WordPress SQL Injection Protection Plugins
1. What is SQL?

Before understanding what happens in a WordPress SQL injection, you need to know SQL.
SQL stands for Structured Query Language, and it’s a programming language. It’s used to communicate with databases, and if you have more than a surface knowledge of WordPress, you know it uses databases for nearly everything. WordPress uses MySQL, open-source software that allows you to access your database and all the info stored in it.
2. Why It’s Important to Guard Against WordPress SQL Injection Attacks

A WordPress SQL injection attack is someone trying to hack your site. There could be several reasons behind this, but one of the most prevalent is to steal your user data. Depending on your site and your site visitors, you may have a lot of valuable info stored.
According to OWASP (Open Web Application Security Project), injection attacks rank in the Top 10 of their Web Application Security Risks list. And although things have gotten better in the last 5 years—likely because more users like yourself are learning to guard against WordPress SQL injection attacks—they are still an issue.
In 2017, injections ranked as the #1 risk. In 2021, they moved down to the #3 position.
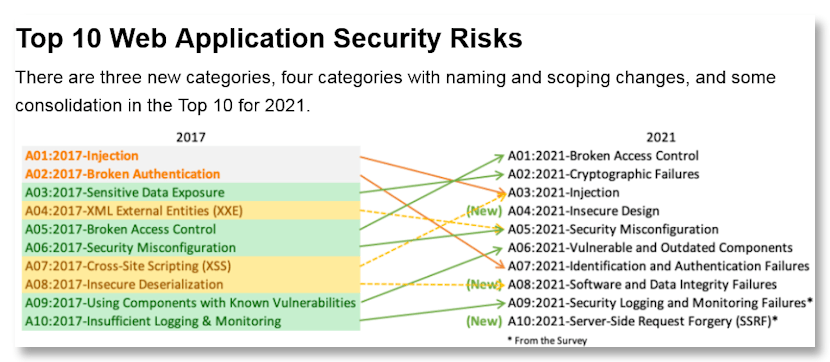
Source: OWASP
The risks don’t stop at stolen user data. Your entire WordPress installation could be destroyed. Of course, if you have been keeping up to date with your WordPress Management and staying on top of basic things like regular backups, all is not lost. But you could still face downtime and you’ll have to face the issue of your user’s personal info now being in the hands of hackers.
According to OWASP, the main consequences of a WordPress SQL injection—actually, an injection on any platform—will undermine the following.
- The confidentiality of the sensitive data you store in your databases
- A lack of authentication of user names and passwords can lead to
So attacks have some scary consequences. As mentioned above, your data could be compromised in several ways. Tampered with and changed, copied and stolen, or deleted. Or a hacker could deface your site.
These are excellent reasons for making sure you take regular backups of your site. And since an injection attack could be used to plant malware, using malware scanning software is a good idea as well. Franky, you should be taking any and all steps you can to manage your WordPress site.
But what exactly is a WordPress SQL injection attack?
3. What is a WordPress SQL Injection Attack?
SQL injections aren’t limited to WordPress. Since they target databases, any web application that uses a database is vulnerable. They’ve been around for years—more than 20. And they are a favorite of hackers. In fact, a State of the Internet Report done by Akamai a few years ago says that between 2017 and 2019, just over 65% of all attacks against software applications were injection attacks. Clearly, they are a serious threat.
An SQL injection—commonly called an SQLi—is when a hacker interferes with SQL queries. This allows them to access and manipulate data they shouldn’t be able to see. This could be data input by users or any data that the app has access to. It’s even possible for a hacker to comprise the server or any backend infrastructure that exists behind the app or platform.
4. How Does a WordPress SQL Injection Attack Work?

As mentioned above, a WordPress SQL injection works by hackers accessing your database using malicious SQL statements. A query is a type of statement. A statement is anything that the database recognizes as a valid command, but a query is what will return the requested records.
An attack can be performed using several methods. Here are a few examples.
Always True SQL Statements
In SQL, always true is defined as 1=1, because 1=1. That’s always the correct answer, so it’s a true scenario or condition. This typically isn’t used alone. There would be an AND, WHERE, or OR added to the query.
Batched SQL Injections
Nearly every database supports batched SQL statements, which simply means a statement that’s a group of statements—two or more—separated by a semicolon.
However, there are also different types of injection attacks.
Types of WordPress SQL Injections Attacks
There are multiple types of injection attacks, and depending on a hacker’s objective, they will use whatever yields the results they want.
In-Band SQL Injection
Powerful yet simple, this type of injection attack allows the hacker to insert and retrieve the results from the same channel.
There are two forms of In-Band injection attacks.
Error-based attacks. The first level of this intrusion is something of a fishing expedition. The hacker is looking for useful information about the structure of the database and the names of tables. With that info, they have what they need to formulate new attacks.
Union-based attacks. The union is an SQL operator that combines the results of two or more statements. So a hacker could extract results from multiple tables.
Inferential SQL Injections
Also known as a blind injection, the object here is to find answers to true and false queries to find out more about the database. There are two types of Inferential SQL Injections. They are:
Boolean attacks. This technique involves sending a Boolean-based query to the database, which forces different responses, depending on the query. Even though no data is returned, an attacker can determine whether they obtained true or false returns.
Time-based attacks. This attack involves sending a command to the server that forces a delay in execution. Depending on the response time, the query is either true or false.
Out-of-Band Injections
Finally, the out-of-band injection is used if an attacker can’t get what they want via an injection of a single channel. This type of injection can be used as an alternative to the inferential type of injection.
5. How to Prevent an SQL Injection
Now that you know what injections are and how they are used on your site, how do you protect your site and prevent a WordPress SQL injection—or an injection on any platform that uses a database?
Here’s a key method of preventing an injection attack.
Prepared Statements
A prepared statement will execute repeated SQL statements. They can be the same or similar statements.
Using prepared statements in concert with variable bindings or parameterized queries should be a basic skill of any developer. When using this technique, developers must initially define all of their SQL code and then pass in the parameters. This keeps the code and the data separate and distinct and denies hackers the ability to change the intent of a query—from something legit to something else.
Now let’s get a bit more specific and deal with what you can do to prevent a WordPress SQL injection.
How to Prevent a WordPress SQL Injection
Here are several steps that are good practices. And as always, before making any changes to your site, I recommend you do a backup of your core files and databases.
Use input validation and filtering. Many sites require users to submit data, which is the easiest way for hackers to gain access to it. So make sure all user data is validated and filtered, meaning you test all data that users submit.
Avoid Dynamic SQL. Dynamic SQL is constructed to use at runtime, while static or embedded SQL is compiled ahead of time. When using dynamic SQL is necessary but it’s also often inefficient and creates vulnerabilities. Instead, use the prepared statements mentioned above.
Keep Your Site Up to Date. One way to increase database security and prevent a WordPress SQL injection is to ensure you keep your site up to date. That means making sure your core files and plugins are always running the latest versions—and this doesn’t mean the latest version of a plugin that was abandoned years ago.
To help with your WordPress maintenance, you can use a tool to handle automatic WordPress updates.
Develop Good Security Practices. This would include making sure you have a good security plugin, using a firewall, and ensuring your site has a valid SSL certificate.
Strip Unnecessary Functionality from Your Database. Don’t give hackers more to work with. If you have content in your database that serves no purpose, remove it.
Be Stingy with Access Privileges. It’s unlikely that every user needs full permissions on your site, so reduce access. WordPress provides a range of predefined roles, including:
- Super admin
- Administrator
- Editor
- Author
- Contributor
- Subscriber
Each of these roles allows the user to perform set tasks.
Encrypt Confidential Data. Nothing is 100% failsafe, so tightening security wherever you can is just good practice. Go a step further and encrypt any confidential information stored in your database.
Keep Personal Information Hidden. Don’t make it easy for hackers to find info from your database error messages. Instead of revealing things like contact information or authentication credentials, consider generic error messages.
6. WordPress SQL Injection Protection Plugins
All that seems like a lot of work, doesn’t it?
The good news is that there are several plugins you can use to protect your databases from attacks. The following is just a tiny sampling of some of the better options.
Wordfence Security

Wordfence offers an array of security measures and is available in a free version plus a premium option that offers additional features.
It doesn’t matter what security plugin you choose, they all seem intimidating at first, but don’t give up. Once you have it downloaded and the settings tweaked to your preferences, you’re good to go. The features include:
- A firewall to block WordPress SQL injections
- Two-factor authentication
- Malware scanning for injection attempts
Sucuri Security

Sucuri is another free security plugin for your WordPress site. It offers several features:
- Security Activity Auditing
- File Integrity Monitoring
- Remote Malware Scanning
- Effective Security Hardening
They also have a premium version which includes their Website Application Firewall (WAF), which further to protects your site from a WordPress SQL injection attack.
Conclusion
As pointed out, SQL vulnerabilities have been around for decades, but that doesn’t mean they’re any less dangerous. They continue to be one of the most common attacks made against WordPress sites and XSS attacks.
We distilled a lot of information above, but here it is in a nutshell.
In order to protect yourself from SQL vulnerabilities, it’s best to understand how attacks against databases are made. Once you know that, you can implement various methods and strategies to protect your website and valuable data from theft or manipulation.
One of the best ways you have to protect yourself is by keeping your WordPress site up to date, and a great way to do that is to use a maintenance tool like WPBlazer. It will take most of the time and energy out of your WordPress management. Why not give it a try?
